How to update Windows 2012 R2 AD CA from SHA1 to SHA2 or SHA256
Windows 2012 R2 Active Directory integrated by default publish and issue SHA1 certificates, which is now declared as untrusted by Google Chrome. There was warning window during configuration, but who knows it so important, after it is already intergrated you can discover you forget to change default hash algorithm.Windows 2012 R2 out of the box provider is already MS Software Key Storage Provider so you don't have to convert something. It is out of this article, how to install nginx, CA or IIS. To convert storage provider, seek for more complex technet articles like this.
Conversion of CA hash algorithm
To convert Certification Authority and web server certificates form sha1 to SHA 256 it is pretty simple but not so well documented.To convert Certification Authority you just have to type one command. Go to Administrator command prompt.
certutil -setreg ca\csp\CNGHashAlgorithm SHA256
How to Issue Windows 2012 R2 CA sha256 trusted certificate to Graylog ubuntu nginx or apache web server
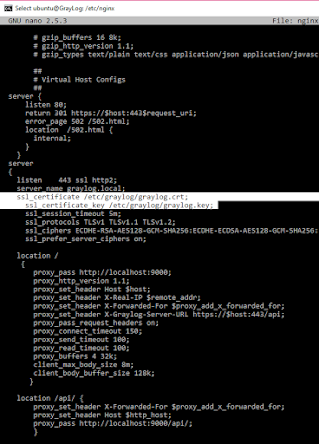
A little bit more complex is request key from linux for nginx or apache server. I already had self signed certificate, but from linux perspective, request is almost the same. To avoid exposure of API and port 9000 I am keeping nginx proxy on graylog server. My nginx configuration is as follows, as you can see, there is nothing changed from graylog perspective.If you don't have key at all you have to first generate a key.
openssl genrsa -out graylog.key 2048You can use old key, and just request certificate.
openssl req -new -key graylog.key -out graylog.csr -new -sha256 -x509The last x509 probably is not necessary, but in case you have old linux/ unix you can type -x509. See the picture
Check if your csr file is present. You can grab it by scp or just copy content in clipboard.
To request certificate with Subject Alternative Names
1.Create Answer file
[ req ]
default_bits = 2048
prompt = no
default_md = sha256
req_extensions = req_ext
distinguished_name = dn
[ dn ]
C=LV
ST=Latvia
L=Riga
O=Organisation
OU=IT
emailAddress=giors@lv
CN = server.lv
[ req_ext ]
subjectAltName = @alt_names
[ alt_names ]
DNS.1 = server.lv
DNS.2 = www.server.lv
2.Request certificate providing answer file
openssl req -new -sha256 -nodes -key server.key -out server.csr -config <( cat csr_details.txt )
Vuala certificate is provided with alternative names
Enroll certificate from Windows 2012 R2 CA
To issue certificate, You must have permissions to Enroll Web certificates. Go to "Certification Authority" mmc, Right click Templates and Choose "Manage".
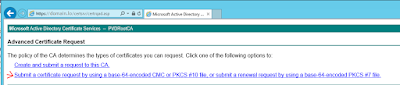
Next go to Your CA web server certsrv page and "Request a certificate"
Next choose "Advanced certificate request"
Choose base-64 encoded
Copy csr file content in Request form and choose web server template. If Web Server Template does not appear, You don't have appropriate permissions.
Confirm request.
Check your certificate details. Rename certificate from cer to crt, Copy it in appropriate location in apache server. Most cases it is /etc/apache2/ssl
Restart your apache or nginx and verify- connection is now secure.
Issue Windows CA trusted certificate to Domain web server
To issue trusted certificate just go to IIS server RootIIS Root→Server Certificates→Create Domain Certificate.
Fill all fields, remember, Common name must match what you type in address in your web browser. Press Finish, you will be asked for Certification authority name and server. Point to Your CA . In case you already had sha1 signed certificate, you just have to push Renew, and certificate turns automatically from sha1 to sha256.
If Workstation is not in domain
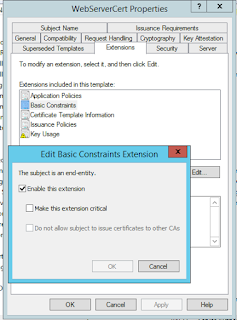
Certificate show problems, if Workstation is not in domain. It is because Root certificate is not installed, in domain Root CA is installed on all workstations via group policy automatically, if web server is accessed from workstation out of the domain, add Basic Constraints extension. It is probably because workstation doesn't know whether server is CA or end point. Go to CA ->Manage templates->Right click on template->Properties.
Make extension critical and vuala it appears on certificate.
Basic Constraints
Besides there must be enabled Basic Constraints, if clients is not installing Root certificate, so browser does not know if cert is CA or not. So to enable Basic Contraints go to Templates->Right Click->Manage->Template->Extensions-Basic Constraints
Name Constraints
Name constraints are allowed suffixes of domain to avoid illegal certificate to be issued.
CAPolicy.inf has to be copied in C:\Windows directory and server must be restarted. Actually it must be placed before install Certification Authority role on server.
[Version]
Signature= "$Windows NT$"
[NameConstraintsExtension]
Include = NameConstraintsPermitted
Critical = True
[NameConstraintsPermitted]
DNS = .domain.com
DNS = .altdomainname.com
email = @email.suffix
UPN = .domain.com
UPN = @domain.com
DIRECTORYNAME = "DC=domain, DC=com"
URL = .domain.com
URL = .altdomainname.com














Nav komentāru:
Ierakstīt komentāru